PicoCTF 2018 Walkthrough 1-16

If you're new to the world of CTFs, or want some simple challenges that won't take hours of commitment to break, PicoCTF is a great starting point. The platforms challenges are short and begin from a low difficulty level - meaning even those new to information security can start here, using nothing more than Google and intuition to make a start. The challenges are divided amongst 5 domains and difficulty slowly increases are point values per challenge increase. You can attempt PicoCTF 2018 here 2018game.picoctf.com
Forensics Warmup 1 | 50pts
Download the flag.zip file.
Navigate to the Downloads folder using cd
Unzip the folder using unzip flag.zip
Use ls to prove the unzip worked. the file flag.jpg should be present.
Attempt to open the file using display flag.jpg. If this fails install the correct software using the command returned in the output.
cd ~/Downloads
unzip flag.zip
ls
sudo apt install imagemagick-6.q16
display glasg.jpg
Forensics Warmup 2 | 50pts
Download flag.png
Use file command to discover flag.png is a jpeg file
Rename file by using mv
Open file with display
file flag.png
mv flag.png flag.jpeg
display flag.jpeg
General Warmup 1 | 50pts
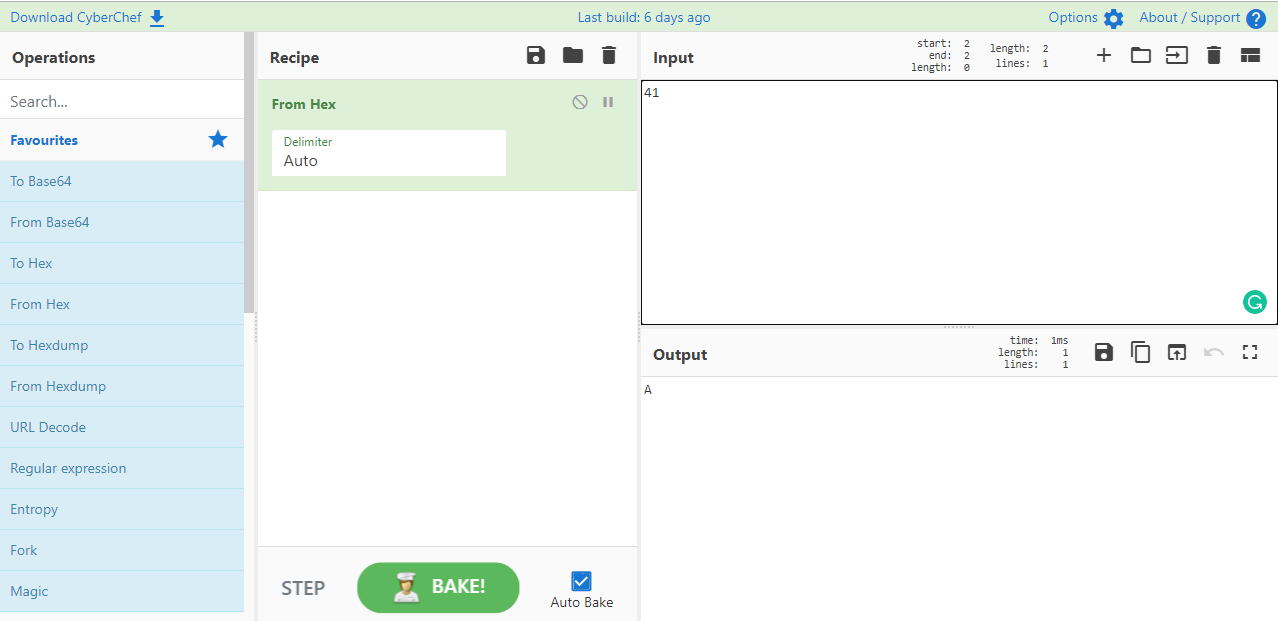
open GCHQ CyberChef
Select from hex to decode text as the recipe
Input '41'
Then type the output 'A' as the flag
General Warmup 2 | 50pts
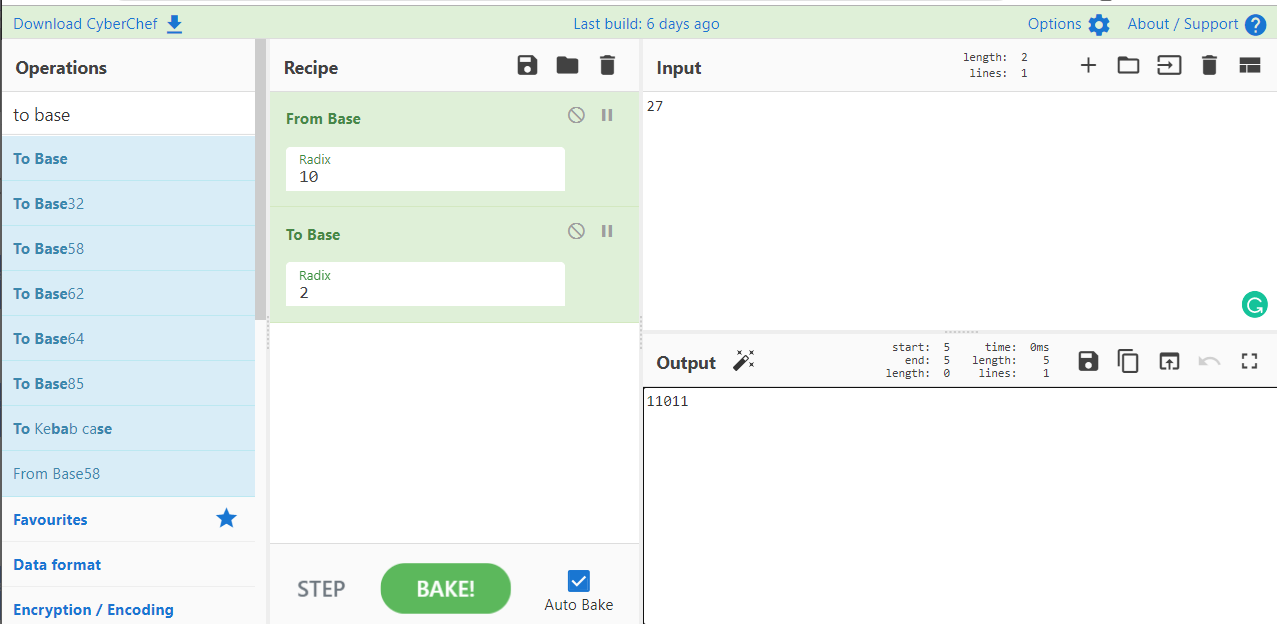
Using GCHQ CyberChef again, select 'from base' and set the value to 10.
Input '27'
The output, '11011' then needs to be inserted within the standard PicoCTF flag format.
General Warmup 3 | 50pts
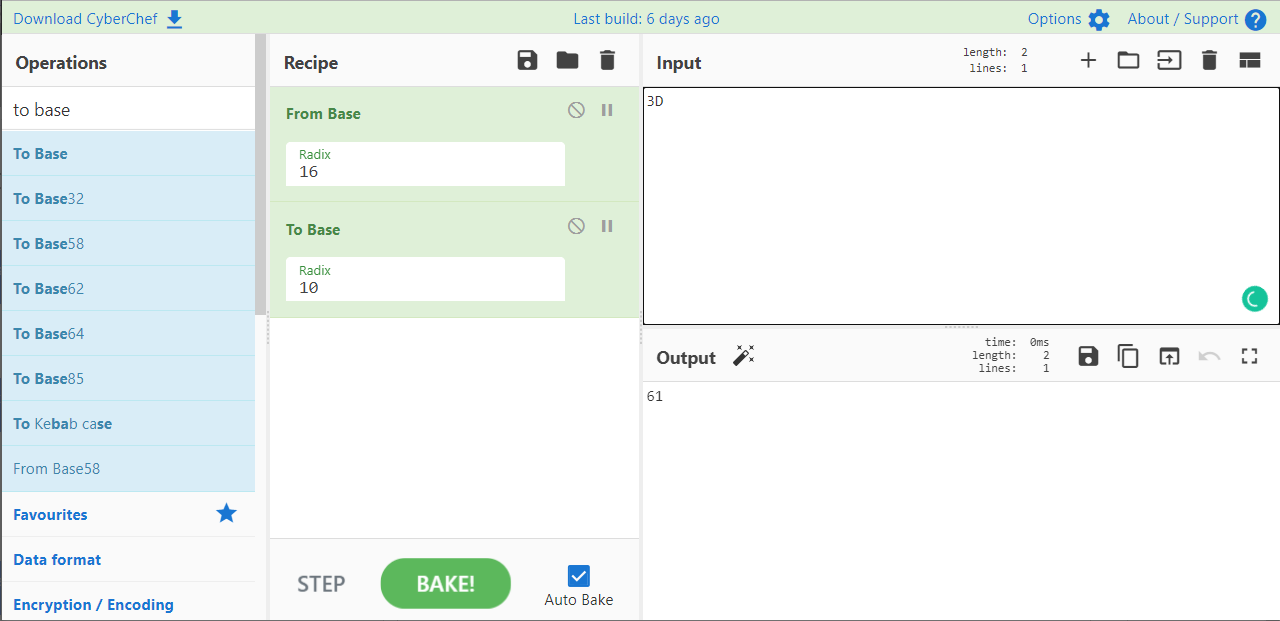
Open GCHQ CyberChef
Select from base and set '16', to base and set '10', as the recipe
Input '3D'
Then type the output '61' as the flag
Resources | 50pts
Simply visit the resources and read to the bottom. there will be a flag at the bottom that can be pasted over. Bonus, can you guess the language the flag is in?
Reversing Warmup 1 | 50pts
Navigate to the desired location using cd
Run the file with ./run
Reversing Warmup 2 | 50pts
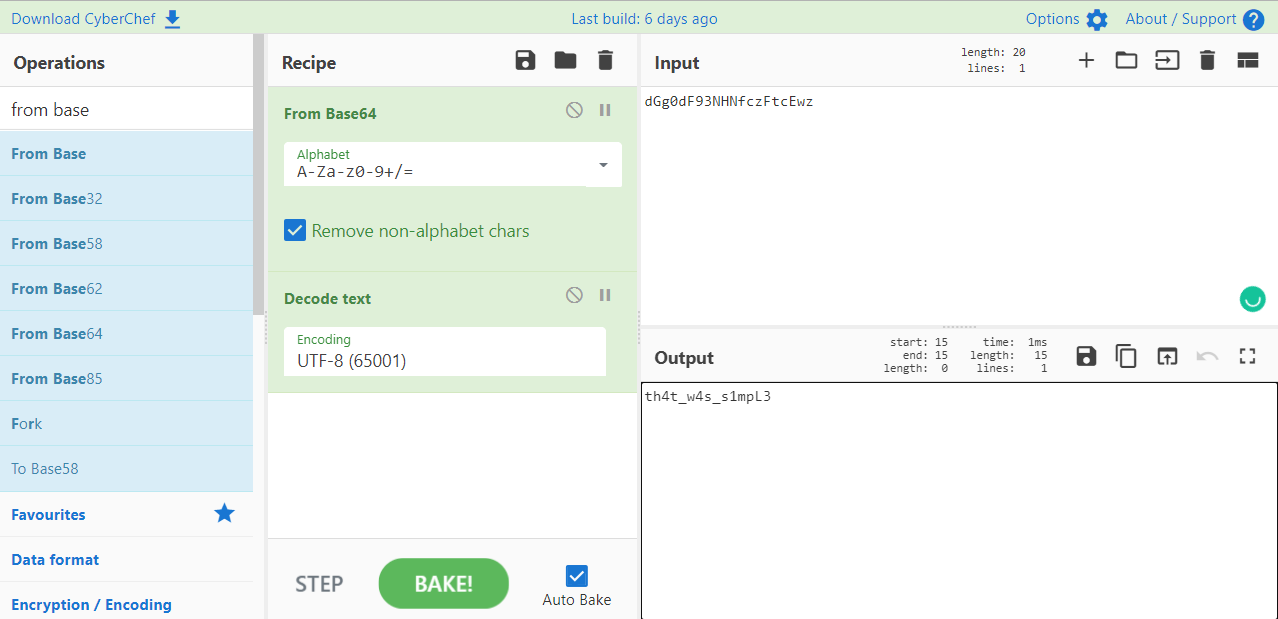
Use cyberchef, setting from Base 64 to Decode Text.
Crypto Warmup 1 | 75pts
Using a Vigenere Decoder, such as the one available on cyberchef, input the string in the input and 'thisisalilkey' as the key.
The output will be the flag.
Crypto Warmup 2 | 75pts
Using a rot13 recipe on cyberchef, input the string.
grep 1 | 75pts
first run the file command on file. This returns that file is ASCII text, with very long lines.
Next run a grep on the file, searching for the "picoCTF" string.
The output is the flag.
file file
cat file | grep "picoCTF"
net cat | 75pts
run the nc command with the params in the solve tab.
Output is the flag.
nc 2018shell.picoctf.com 10854
HEEEEEEERE'S Johnny! | 100pts
First install John the Ripper on the local machine, by running sudo apt install john.
Next, download the shadow file from the picoCTF solve section.
Then source a copy of the rock you wordlist from github.
Then run john with the values above as parameters.
Next log into the shell using the credentials just cracked, the shell will return the flag.
sudo apt install john
john shadow -wordlist:rockyou.txt
nc 2018shell.picoctf.com 35225
root
hellokitty
strings | 100pts
Running file strings shows that the file is a binary file.
Running strings command on the strings file will display the ASCII contents of the bin file. Piping this command to a grep searching for 'picoctf' will return the flag
file strings
strings strings | grep "picoCTF"
pipe | 110pts
nc the reverse shell and pipe output to a grep search
nc 2018shell.picoctf.com 2015 | grep "picoCTF"
Inspect Me | 125pts
View the page source. part one is found in HTML, part two is found on CSS and part three in the js