CTF collection Vol.1 | TryHackMe Writeup

This beginner friendly CTF is a perfect first challenge for those new to CTFs to cut their teeth. If this is your first time or you are stuck on a task, always try googling what it asks and considering the hint before finding the answers on walkthroughs like this one!

#2 What does the Base Said?
Question:
Can you decode the following?
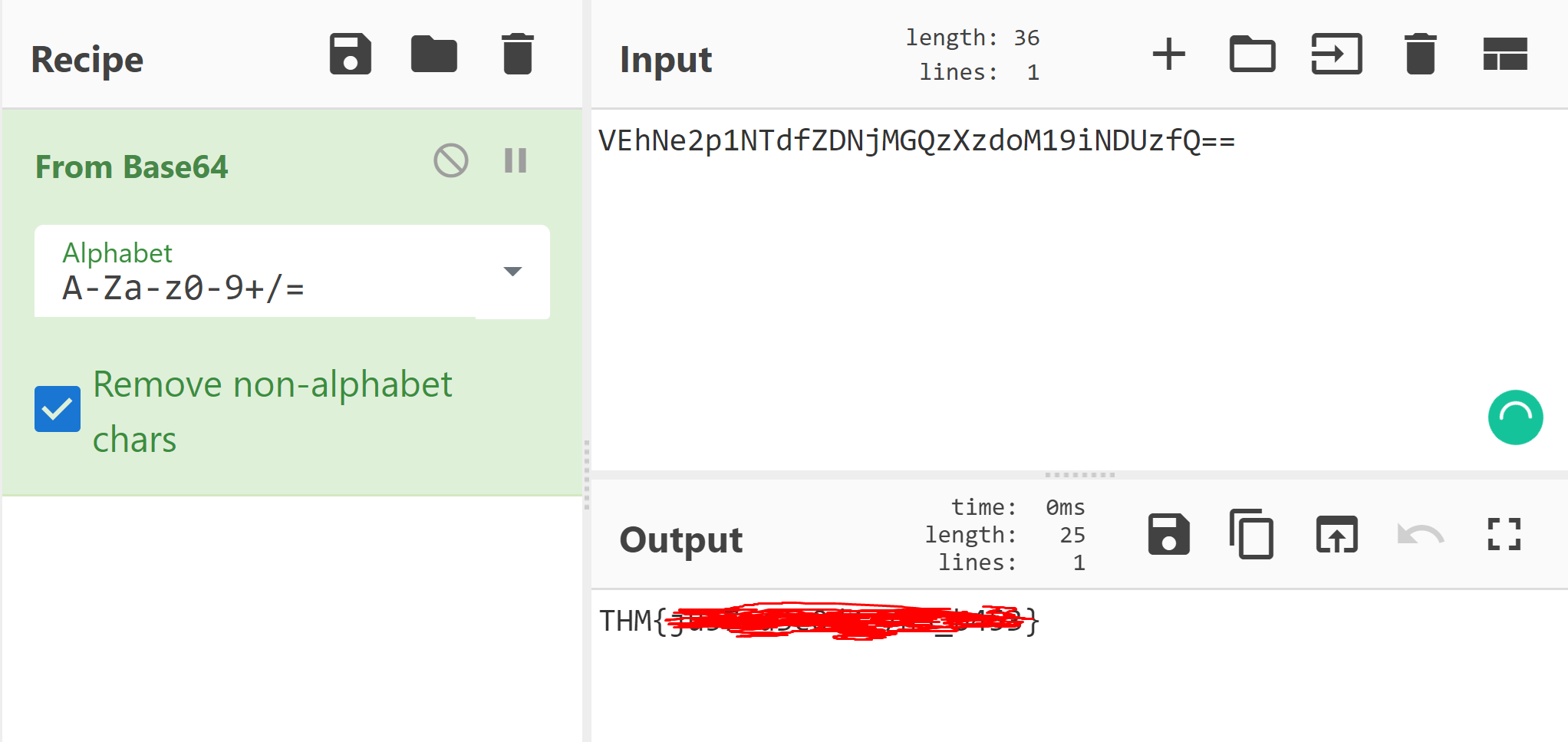
'VEhNe2p1NTdfZDNjMGQzXzdoM19iNDUzfQ=='
Solution:
The name of this challenge gives us a good hint on where to begin, as does the string if you have attempted many CTFs before. This is an encoded string of text, meaning to recover the flag we will need to decode the text. There is a range of tools for perf0rming this - my tool of choice is GCHQs CyberChef.
In order to determine how to decode the string, we need to establish which base it is encoded in. Largely identifying bases comes with time and exposure, but if you're not sure the magic feature on CyberChef can be helpful here.
For more reading on how bases and encoding works, check out this article by Johnathon Cutrell.
#3 Meta meta
Question:
I'm hungry, I need the flag,
Solution:
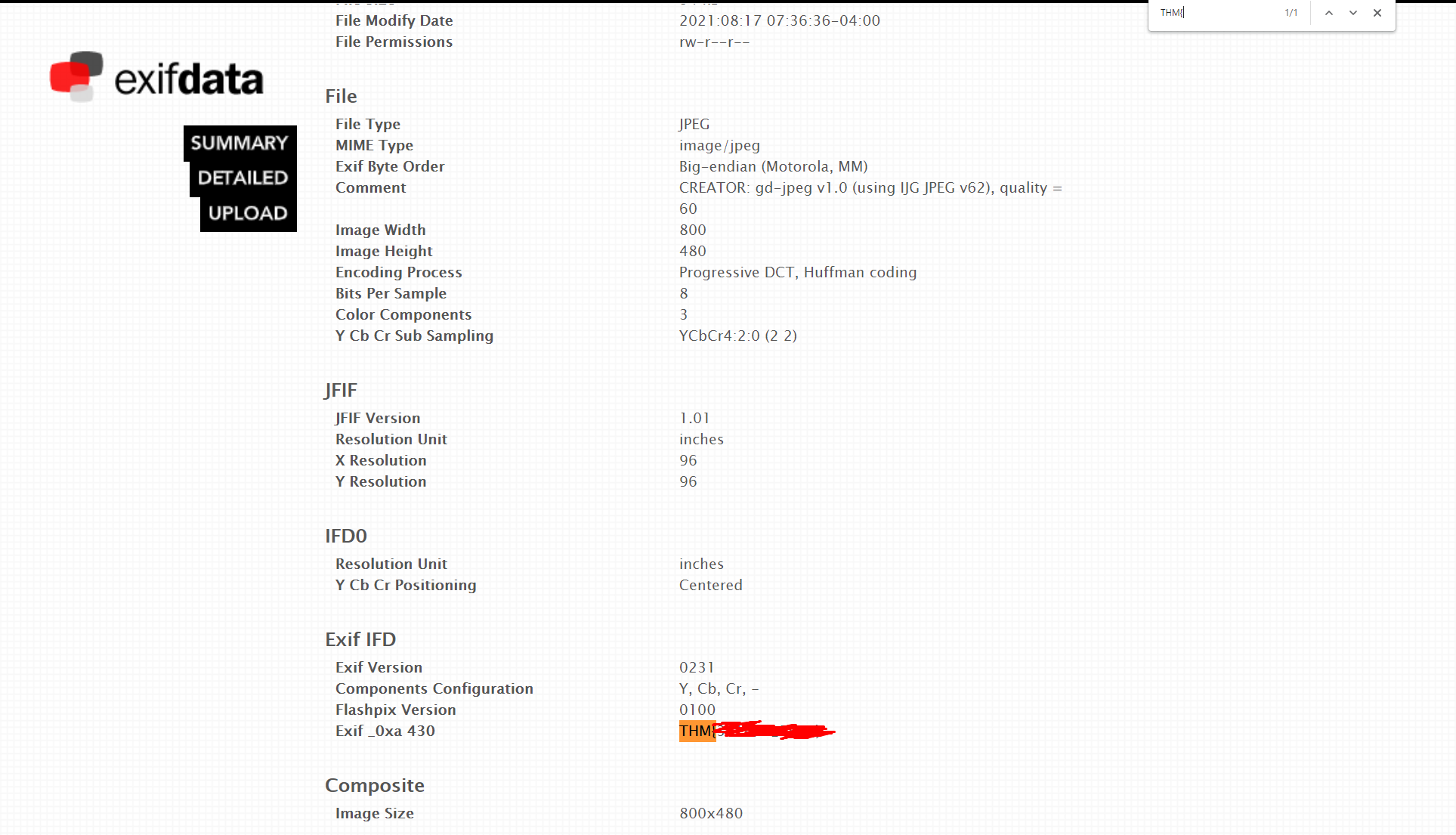
To find this flag, we must search within the metadata, also known as EXIF data, to identify the flag. There are many tools for searching this, depending on your OS - so I have chosen to use a web-based option that is platform agnostic.
Navigate to exifdata.com and upload the file, then hit submit. Once the site displays the EXIF data, you can either manually comb through, or simply search in the page for the known CTF string 'THM{' (see Task 1).
#4 Mon, are we going to be okay?
Question:
Something is hiding. That's all you need to know.
Solution:
This flag is hidden using a technique known as steganography. The most commonly used tool in CTFs for both embedding and recovering steganographically hidden files/statements is a tool called steghide. This tool is both mentioned in the linked article and in the hint for this challenge.
First, install steghide, using the following command in your terminal:
apt-get install steghideThen we use the 'extract' command on the provided file (make sure you have downloaded it and are in the correct directory), and specify an output file. The output file does not need to be created prior to execution.
steghide extract -sf Extinction.jpg -xf steg_output.txt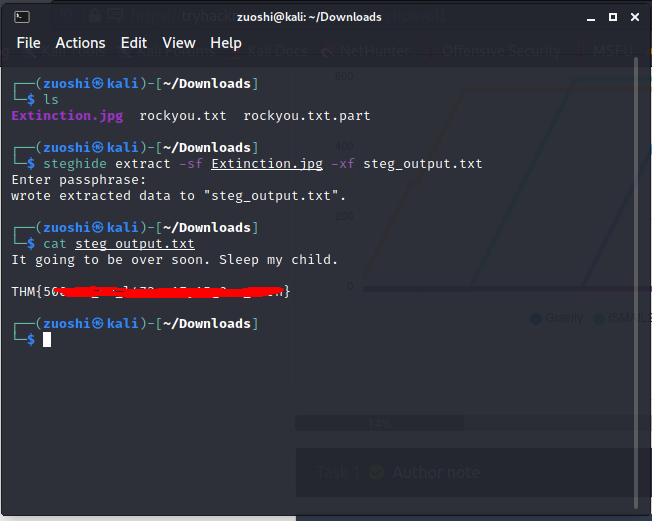
#5 Erm......Magick
Question:
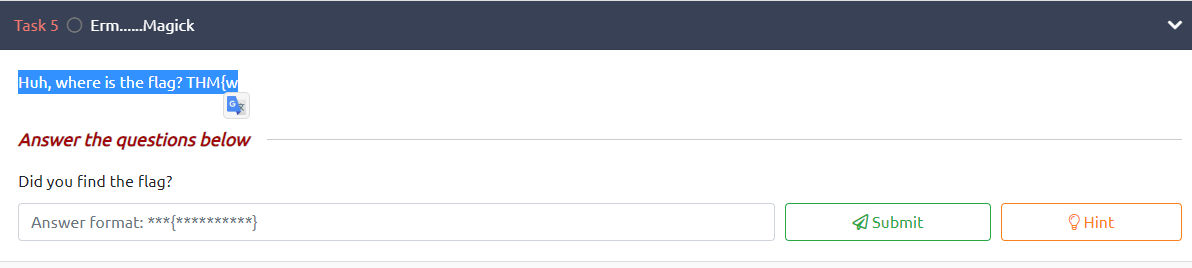
Huh, where is the flag? [REDACTED]
Solution:
This flag is hidden in a very creative - and frustrating - way. As the hint suggests, you can inspect the page source to find the flag. Myself, I accidentally discovered the flag whilst highlighting the question, as I was about to inspect the element. Here the cunning @DesKel obfuscated the flag by changing its colour to blend into the background. Kudos!
#6 QRrrrr
Question:
Such technology is quite reliable.
Solution:
Either by using QR code reading software - or simply scanning the code with a smartphone, you'll be presented with the flag.
#7 Reverse it or read it?
Question:
Both works, it's all up to you.
Solution:
Trying to read the contents of this file using cat or a text editor, we quickly find the file is encoded. Using the file command we can determine this file is an ELF 64 bit binary.
Often with binaries, it's possible for legible strings of text to be hidden within the file, however, combing through the entirety of the file to find these strings is both difficult and time-consuming. A useful tool to help with this is strings. Strings will find all strings within the binary for us saving us some time. Further, to make the task even simpler, we can use grep to search within this output for a known format, i.e. "THM{".
strings hello.hello | grep "THM{"#8 Another decoding stuff
Question:
Can you decode it?
3agrSy1CewF9v8ukcSkPSYm3oKUoByUpKG4L
Solution:
Much like previous challenges featuring encoded strings, we can use CyberChef. Here the string is a Base58 string.
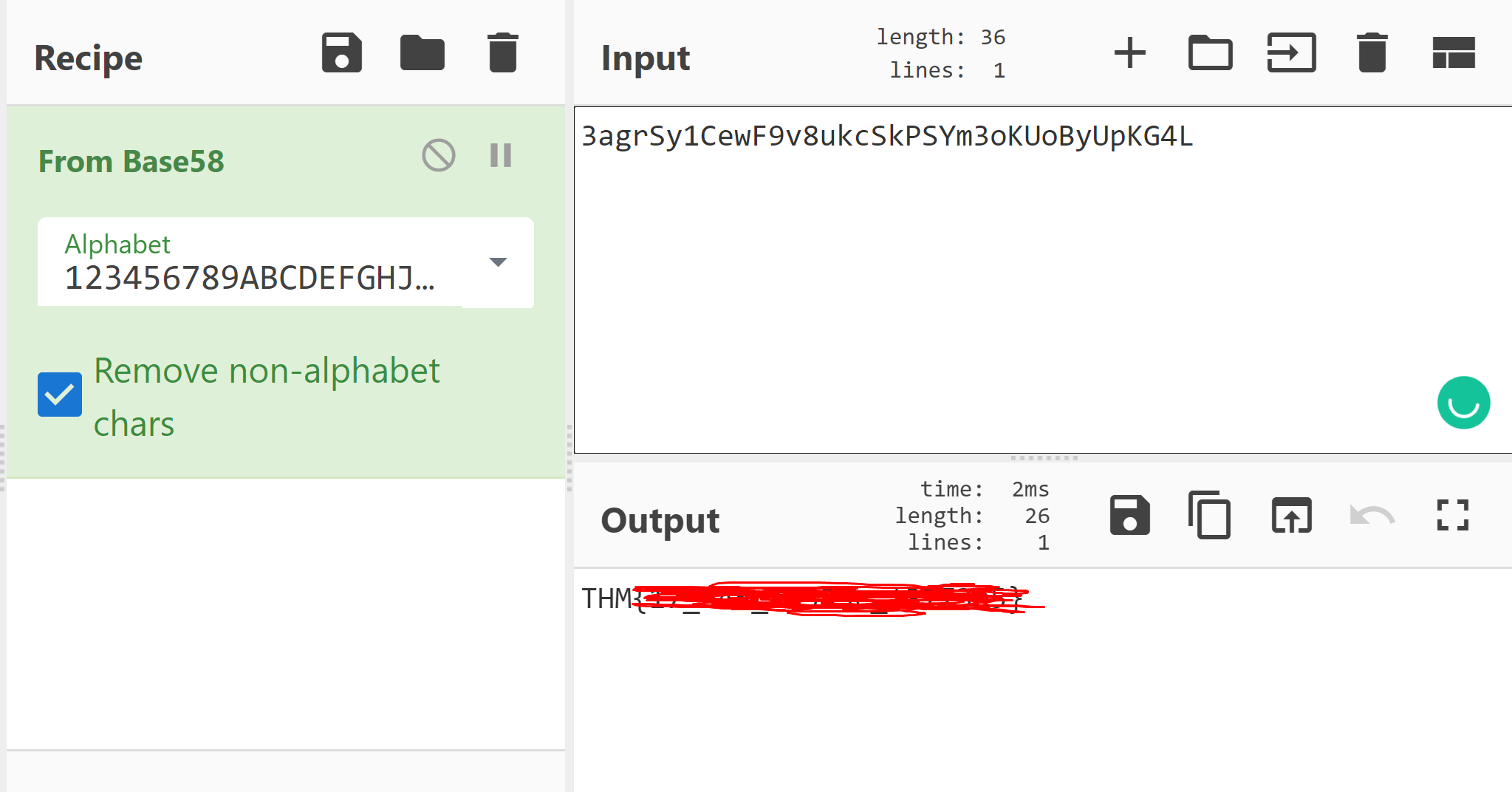
#9 Left or right
Question:
Left, right, left, right... Rot 13 is too mainstream. Solve this
MAF{atbe_max_vtxltk}
Solution:
Much like previous CyberChef challenges, using the hint provided in the question to use a ROT13 cypher.
Here I iterated through the 'amount' of rotations, starting at 0 and increasing until the output resembled a flag.
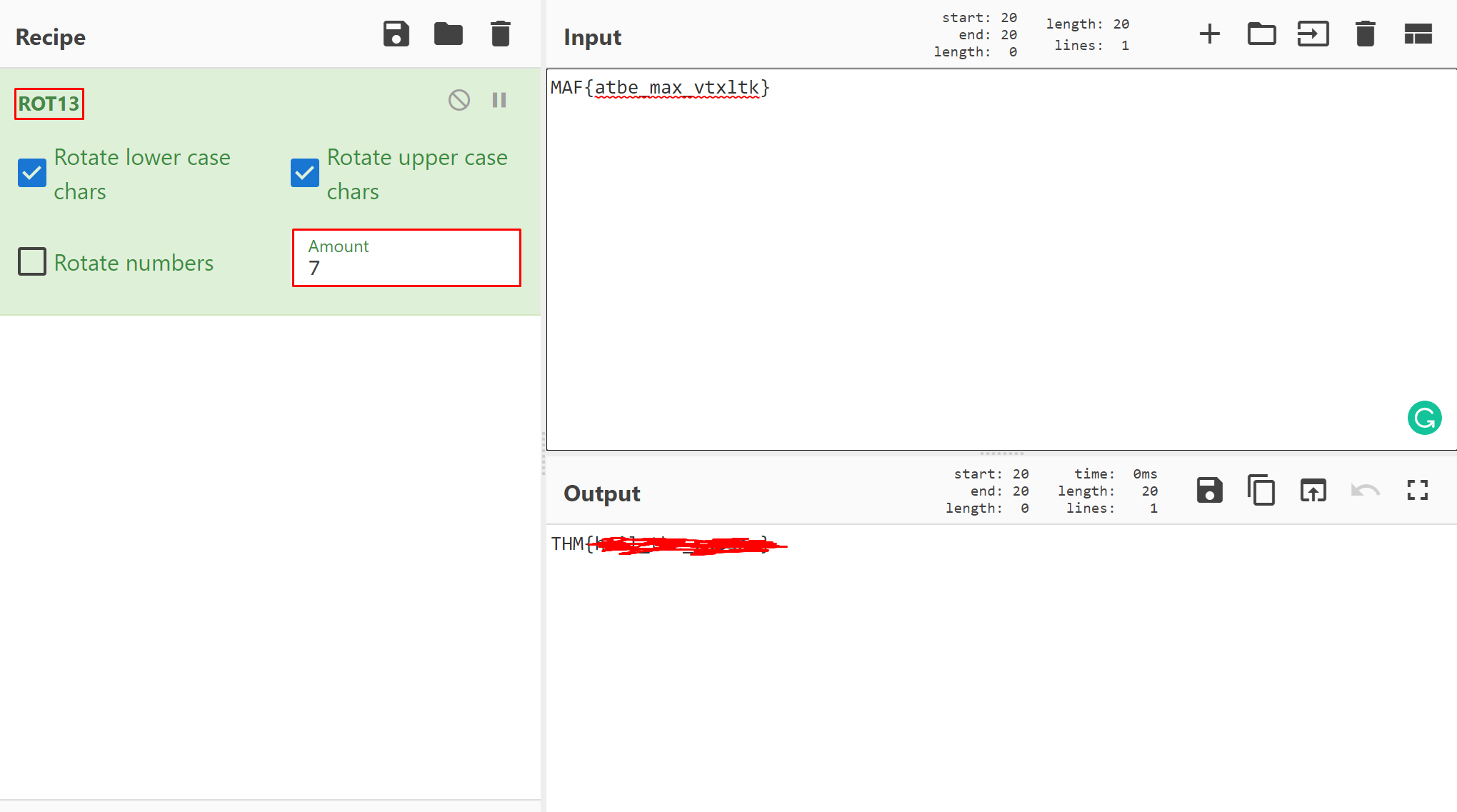
#10 Make a comment
Question:
No downloadable file, no ciphered or encoded text. Huh .......
Solution:
Right-click and inspect element, or enter the developer view, and check the HTML for this question. In one hidden paragraph tag you'll see the flag.
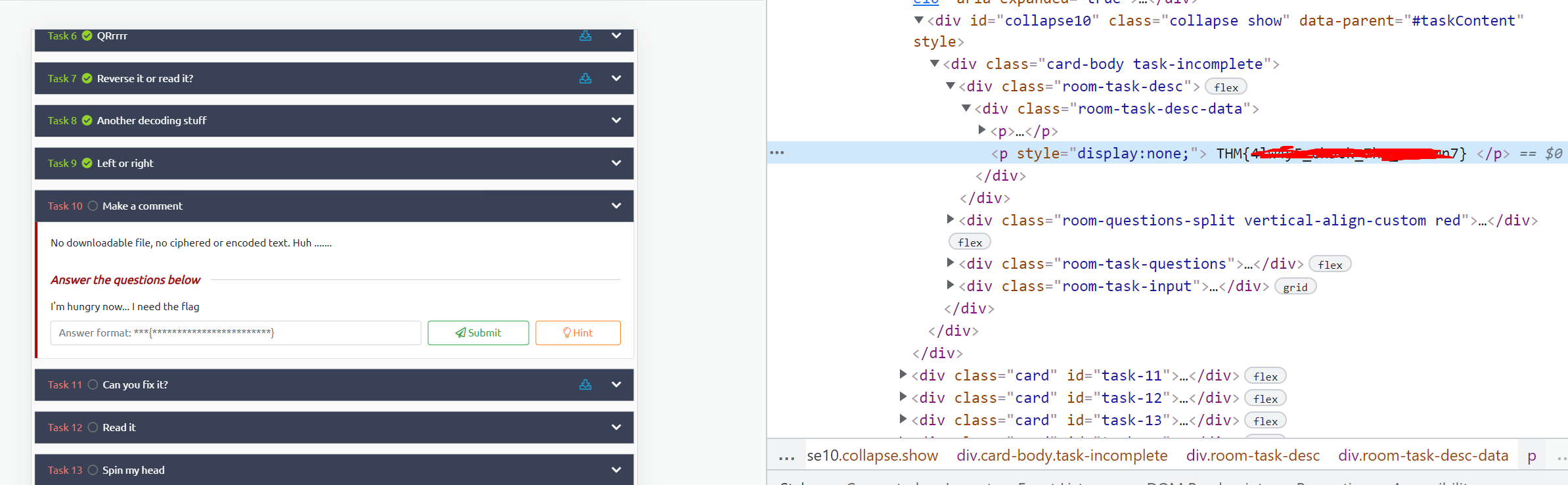
As an aside, this is a normal paragraph tag that has been hidden using inline styles. you can delete 'display:none;' to have the paragraph tag display on the page regularly (which will only remain until you refresh the page.).
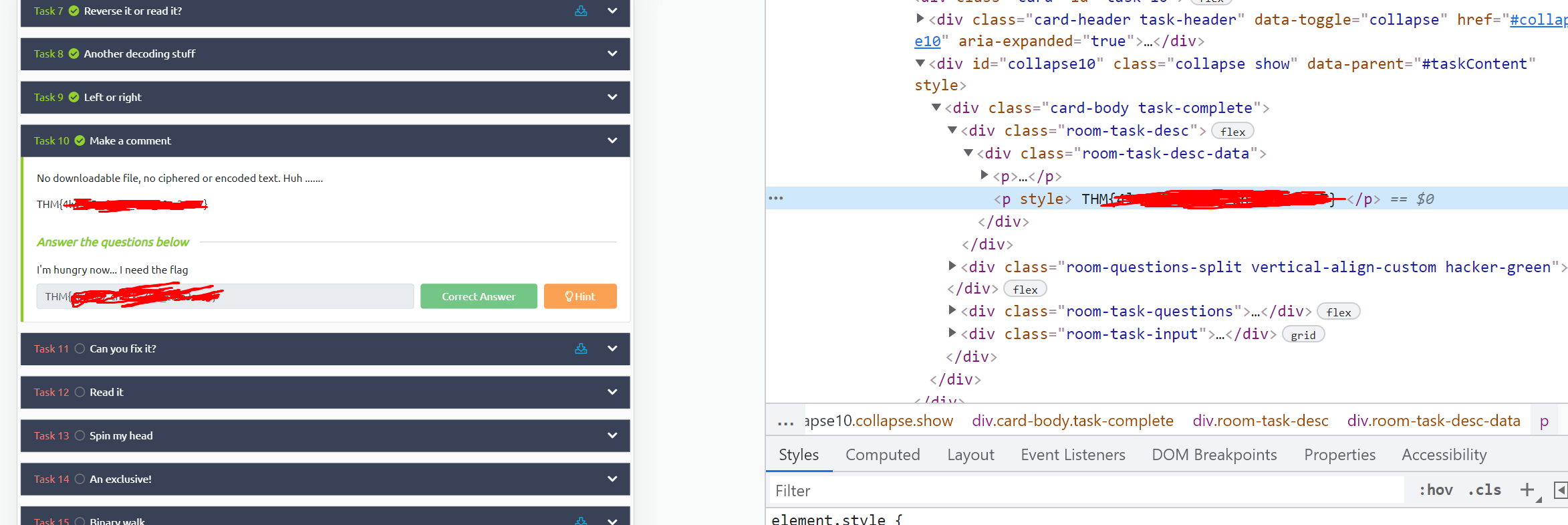
#11 Can you fix it?
Question:
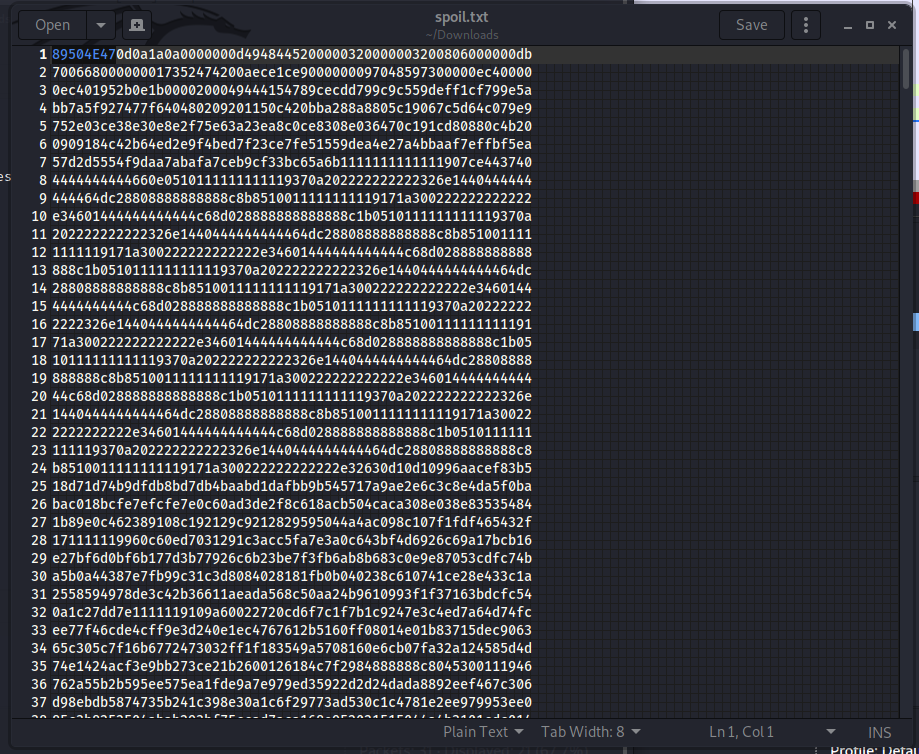
I accidentally messed up with this PNG file. Can you help me fix it? Thanks, ^^
Solution:
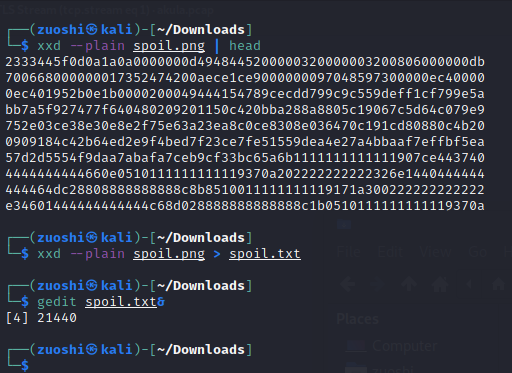
Right-click
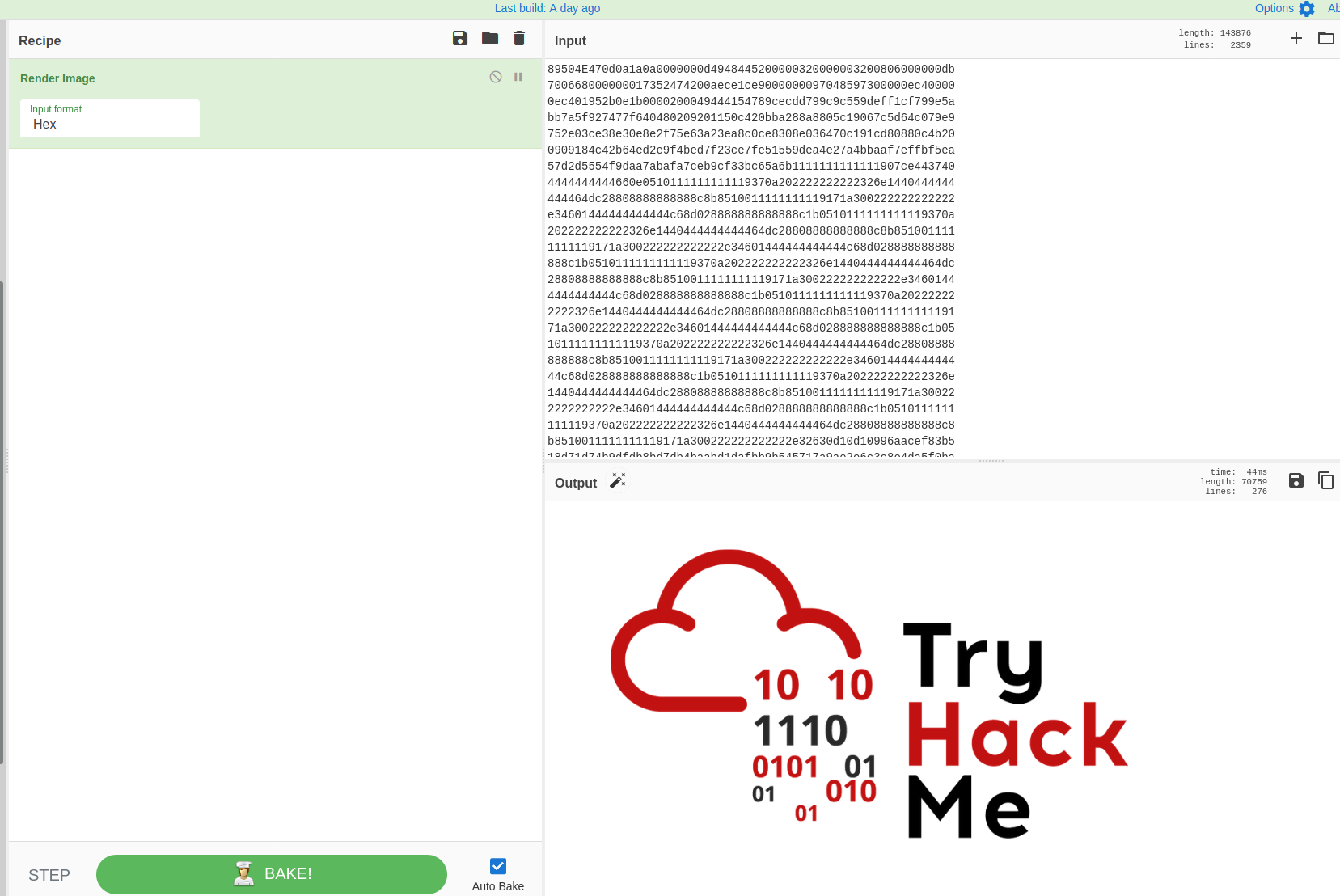
#12 Read it
Question:
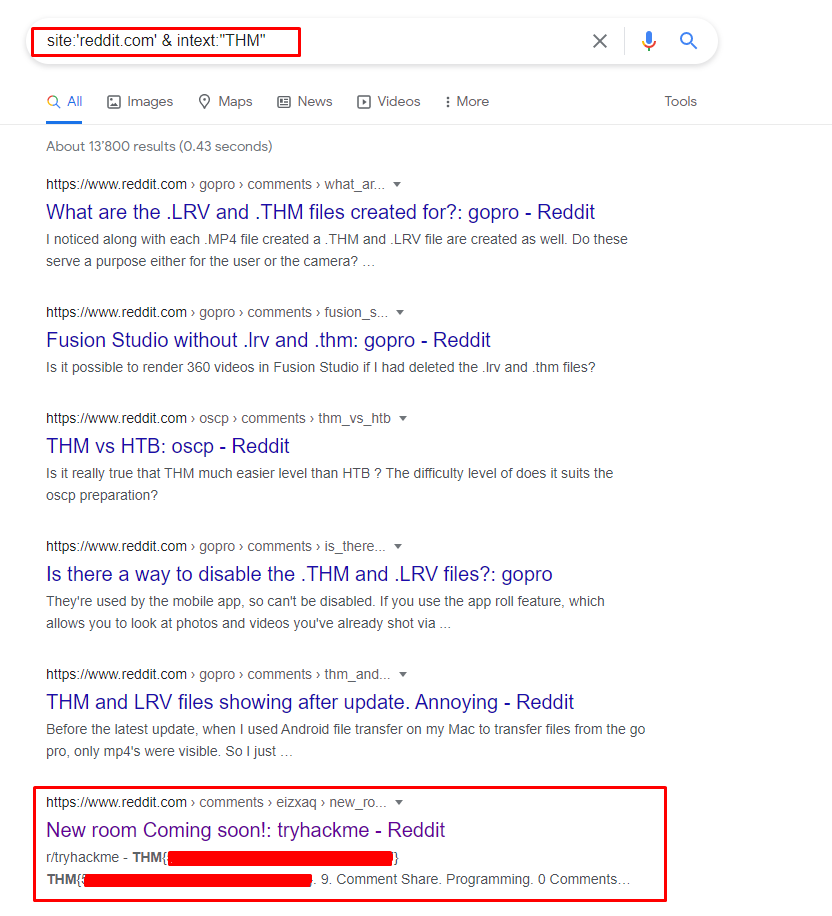
Some hidden flag inside Tryhackme social account.
Solution:
The best method to find this flag is using Google Dorking / hacking.
#13 Spin my head
Question:
What is this?
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>++++++++++++++.------------.+++++.>+++++++++++++++++++++++.<<++++++++++++++++++.>>-------------------.---------.++++++++++++++.++++++++++++.<++++++++++++++++++.+++++++++.<+++.+.>----.>++++.
Solution:
This one led to a trip down internet rabbit holes a little while longer than I care to admit. Seeing the hint 'binaryfuck', I tried to learn more about BinaryFuck and read this short Esolangs Article - which neatly shows a comparison chart of BinaryFuck to BrainFuck. This comparison chart, showing symbols like '+, <, >, -' etc. highlighted that this string must in fact be BrainFuck, BinaryFucks inspiration. Using this, I searched online for a BrainFuck decoder and pasted the string, resulting in the flag.
As an aside, both Esolangs and DCODE prove to be very interesting and comprehensive reference resources if you're curious about cryptography and obscure programming languages.
#14 An exclusive!
Question:
Exclusive strings for everyone!
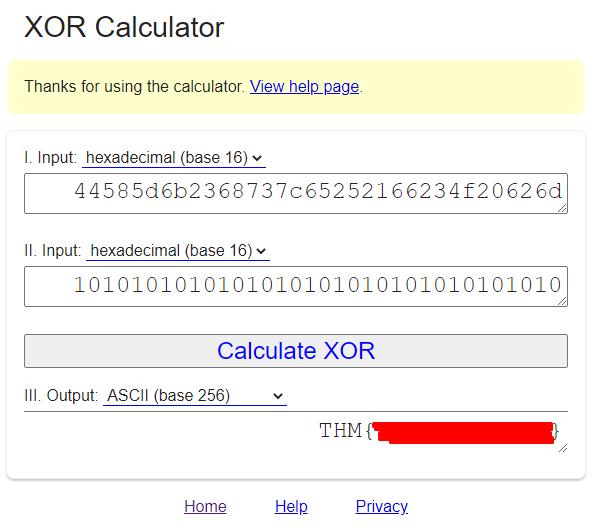
S1: 44585d6b2368737c65252166234f20626d
S2: 1010101010101010101010101010101010
Solution:
The title of this room hints at XOR - or 'Exclusive OR', a logical flow operator. For this I simply searched for an XOR calculator online, pasting both strings in as hex values, with the output conveniently converted to ASCII, resulting in the flag.
#15 Binary walk
Question:
Please exfiltrate my file :)
Solution:
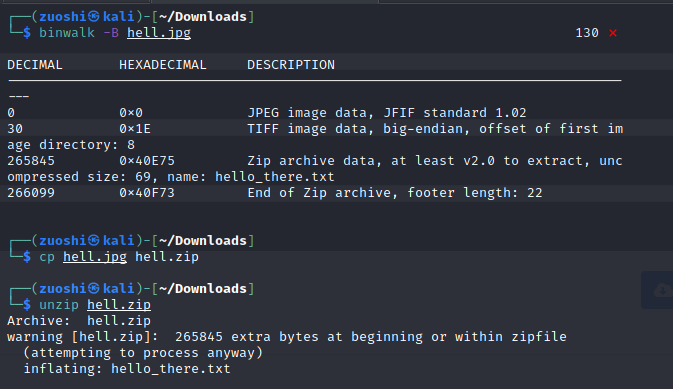
then
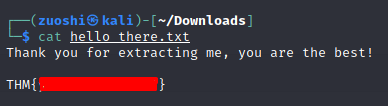
#16 Darkness
Question:
There is something lurking in the dark.
Solution:
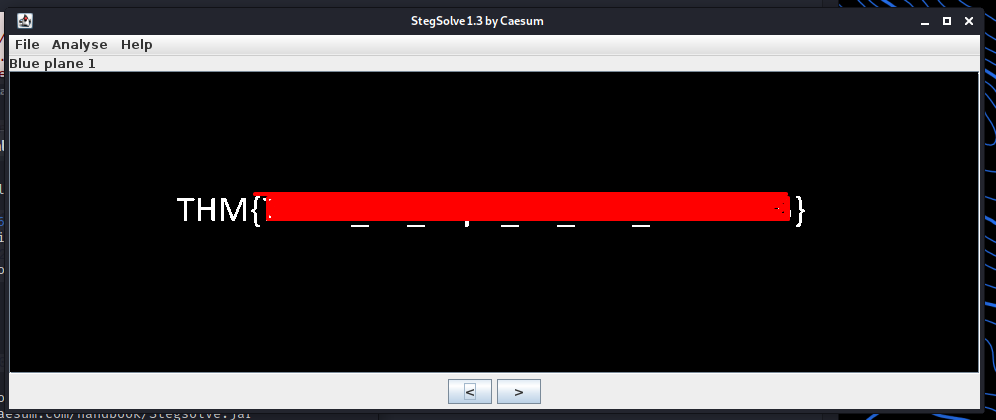
Solving this challenge involves analysing the image in Stegsolve, software that isolates different colour channels.
To download Stegsolve, enter the first set of commands, then run Stegsolve with the final command.
When the software runs, you can cycle through the different colour channels using the arrow buttons. Continue to cycle through until you find a result that is interesting. After cycling through I found the flag on Blue Plane 1
wget http://www.caesum.com/handbook/Stegsolve.jar -O stegsolve.jar
chmod +x stegsolve.jar
java -jar stegsolve.jar
#17 A sounding QR
Question:
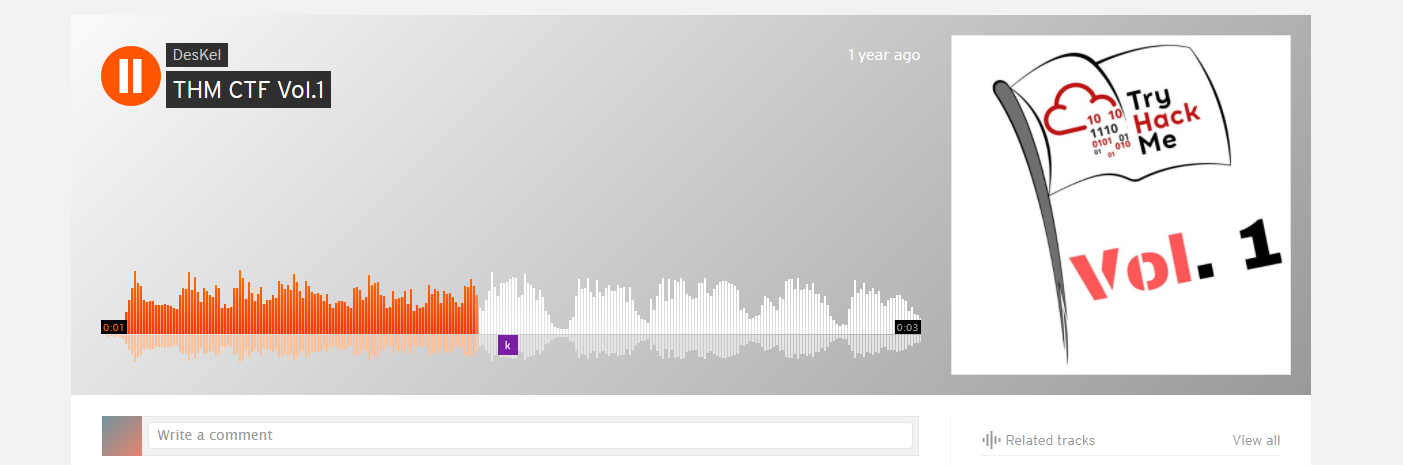
How good is your listening skill?
P/S: The flag formatted as THM{Listened Flag}, the flag should be in All CAPS
Solution:
A very simple challenge to solve, using a QR code reading app or tool, scan the QR. The QR code will direct you to a SoundCloud page. Listen carefully to the track and enter the flag in all caps.

#18 Dig up the past
Question:
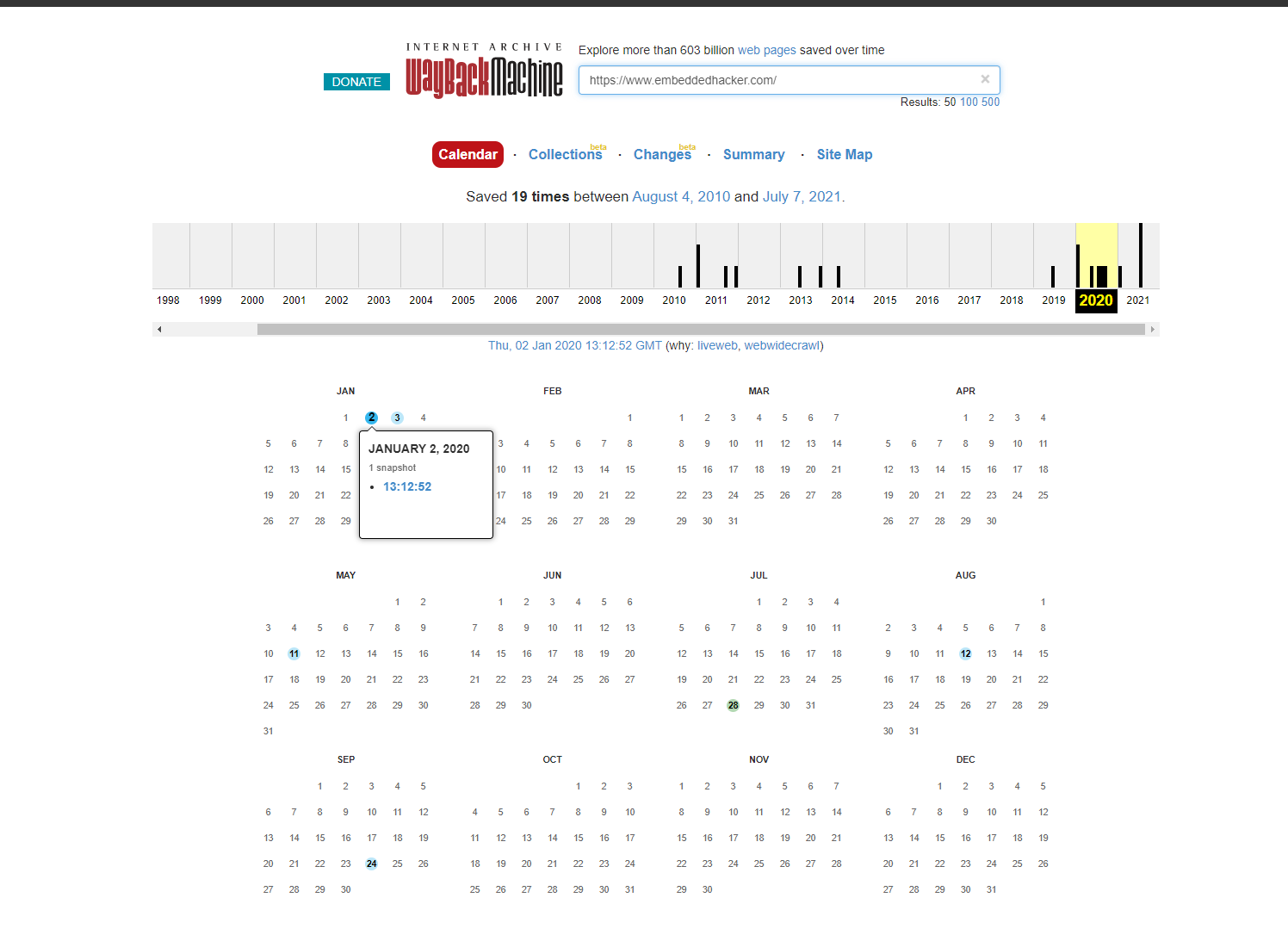
Sometimes we need a 'machine' to dig the past
Targetted website: https://www.embeddedhacker.com/
Targetted time: 2 January 2020
Solution:

#19 Uncrackable
Question:
Can you solve the following? By the way, I lost the key. Sorry >.<
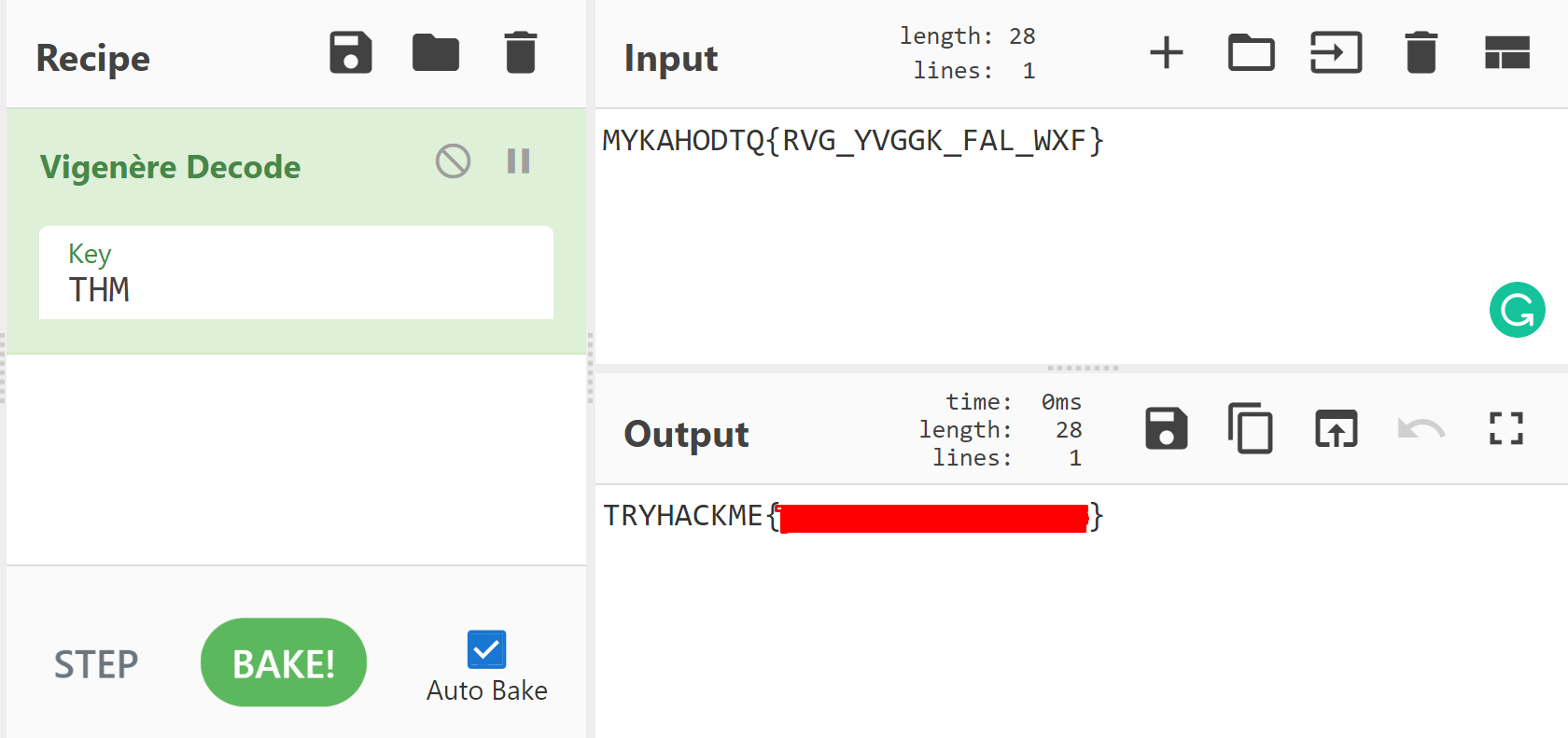
MYKAHODTQ{RVG_YVGGK_FAL_WXF}
Flag format: TRYHACKME{FLAG IN ALL CAP}
Solution:
This challenge requires us to guess the key to a Vigenere cipher. Whilst it could be possible to write a script to brute force possible keys, and searching for any results that matched the known 'TRYHACKME{xxx_xxxxx_xxx_xxx}' format, I instead opted to guess a few values first.
#20 Small bases
Question:
Decode the following text.
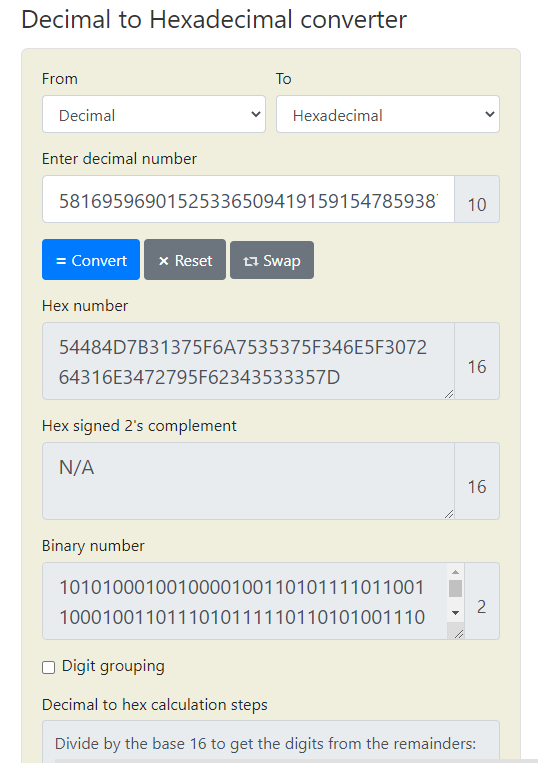
581695969015253365094191591547859387620042736036246486373595515576333693
Solution:
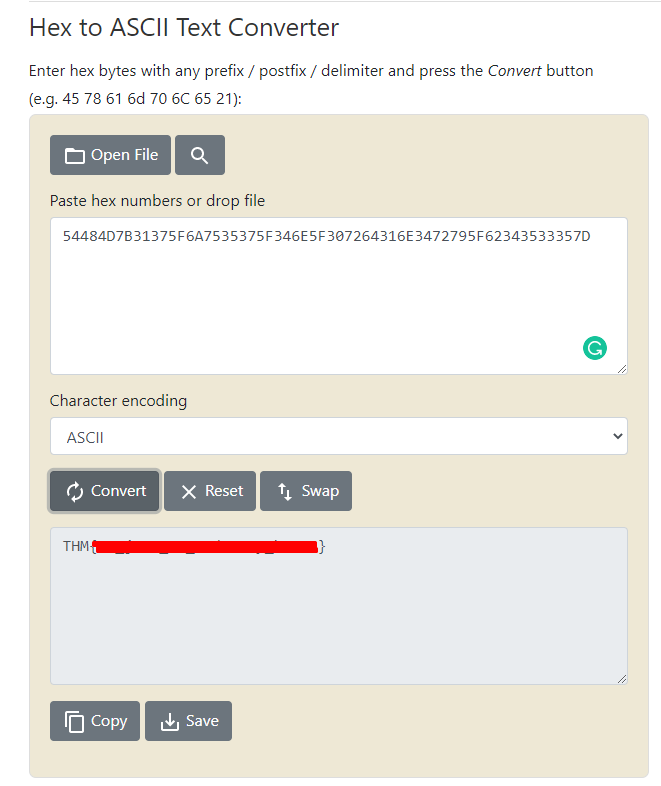
As the hint suggests, here we need to convert from decimal to hex, then from hex to ASCII.
For some reason, I couldn't figure this conversion out in CyberChef - so instead I searched for a decimal to hex decoder and found RapidTables. First pasting the given string value into a dec to hex converter, then copying the output of that into a hex to ASCII converter.
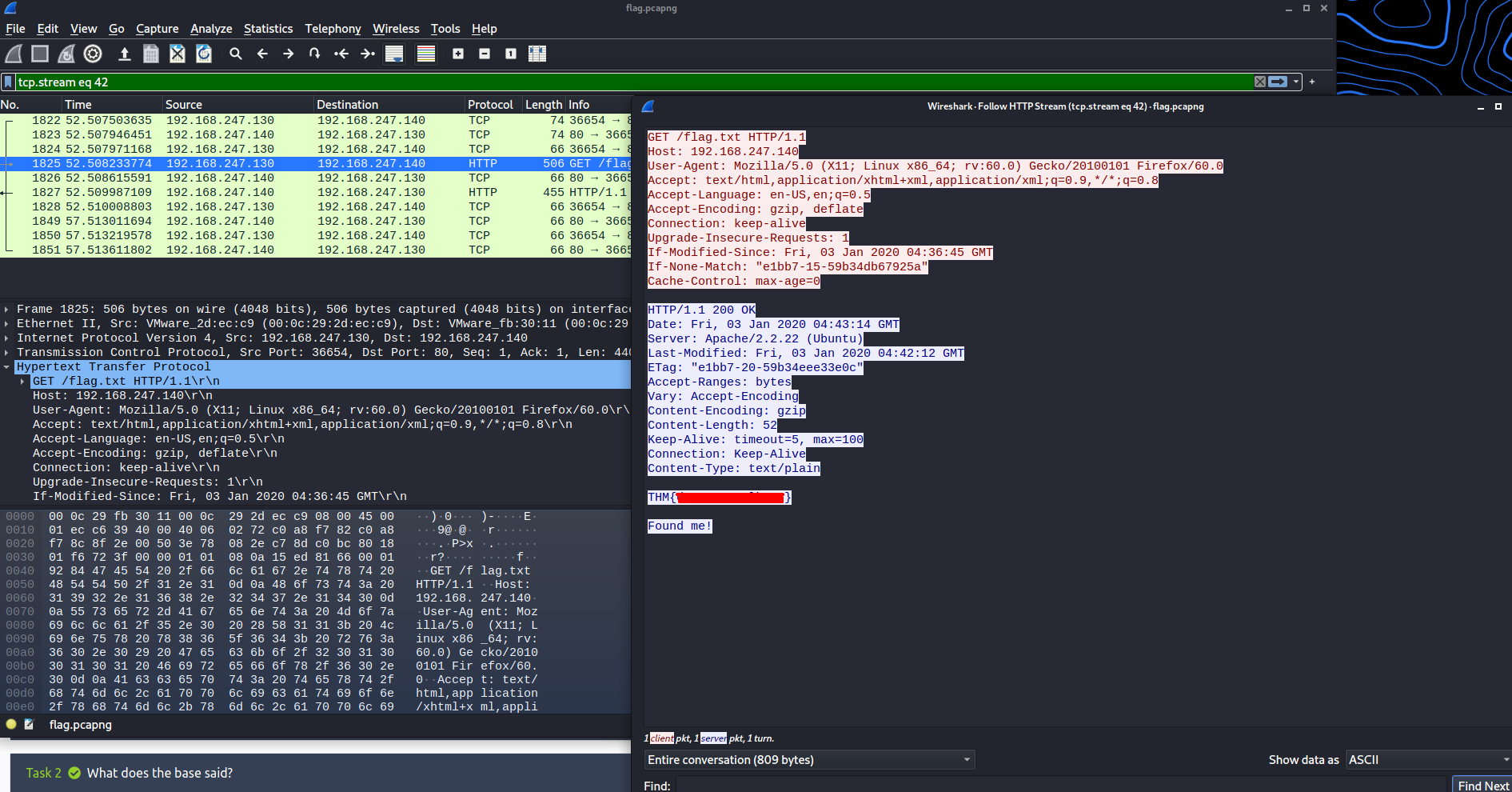
#21 Read the packet
Question:
I just hacked my neighbor's WiFi and try to capture some packet. He must be up to no good. Help me find it.
Solution:
To find this flag we need to first open the pcap file in Wireshark. I managed to find two different methods of finding the flag. The first method involved exporting content, and selecting HTTP objects. When presented with the export menu we can see at the bottom a file named flag.txt. Selecting this shows the flag in the image. Highlighting this file, hit Preview and you will see the flag.
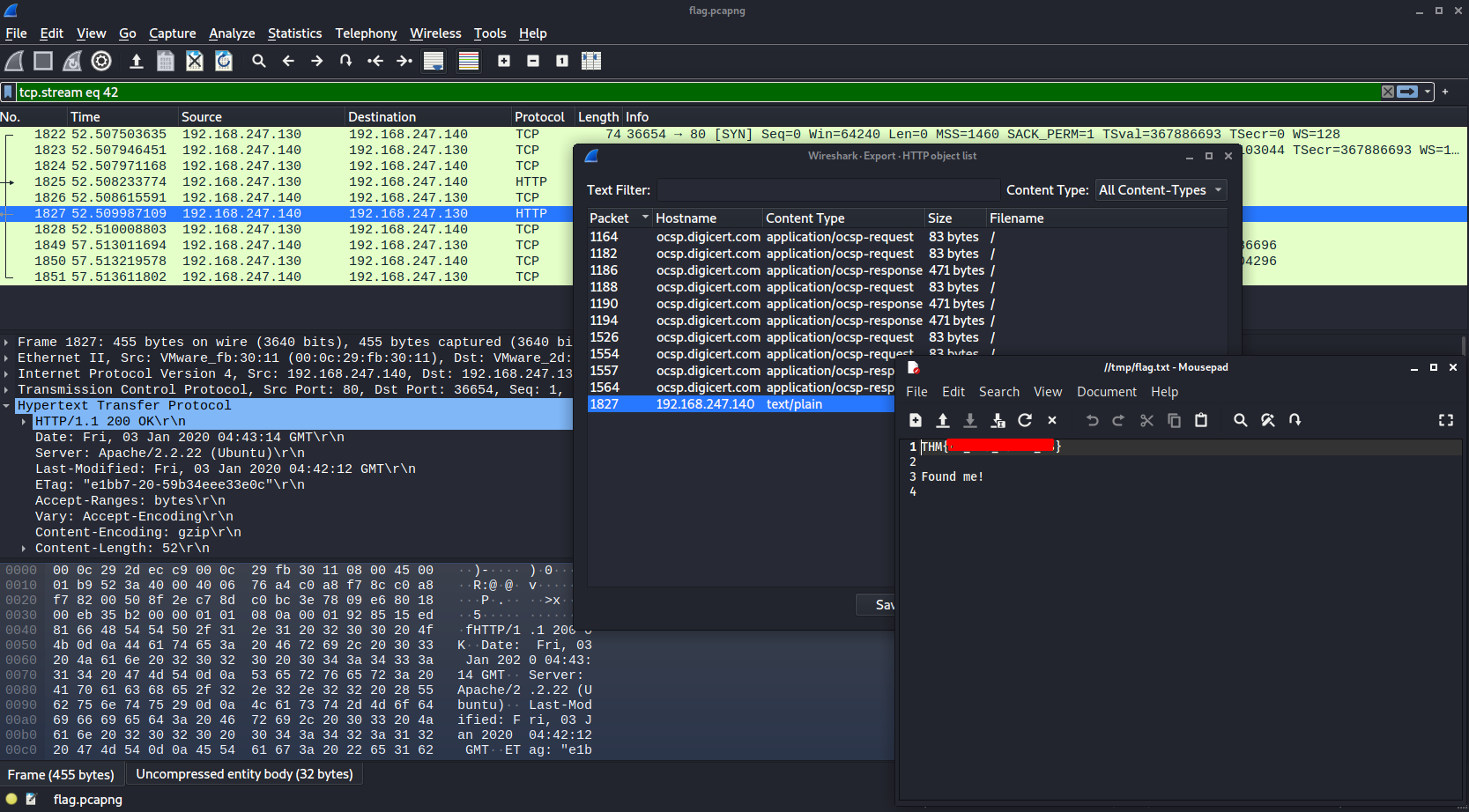
The second method available involved using a filter to highlight http GET requests and following the stream with the flag.
http.request.method == GETUsing this filter returned just one result, flag.txt. Right-click this result and select 'follow stream' then 'HTTP' and the output with the flag will be shown.
Thats it! This CTF is a great opportunity for beginners and experienced hackers alike to practise and improve CTF skills.
If you want to read more CTF walkthroughs and InfoSec related tutorials and articles, don't forget to subscribe to the CertiFried IT newsletter.
